The COVID-19 Cybercrime Spike & How It Will Impact the Fraud Landscape
As much of the world finds itself under stay-at-home orders, traditional criminals are forced off the streets. Crime rates are down 28% in the United Kingdom, with double-digit declines across most of the United States as well. But cybercriminals are unaffected, continuing to operate from the safety of their homes, and will stop at no ends to exploit fear and confusion. The result: off-the-chart rates of cybercrime.
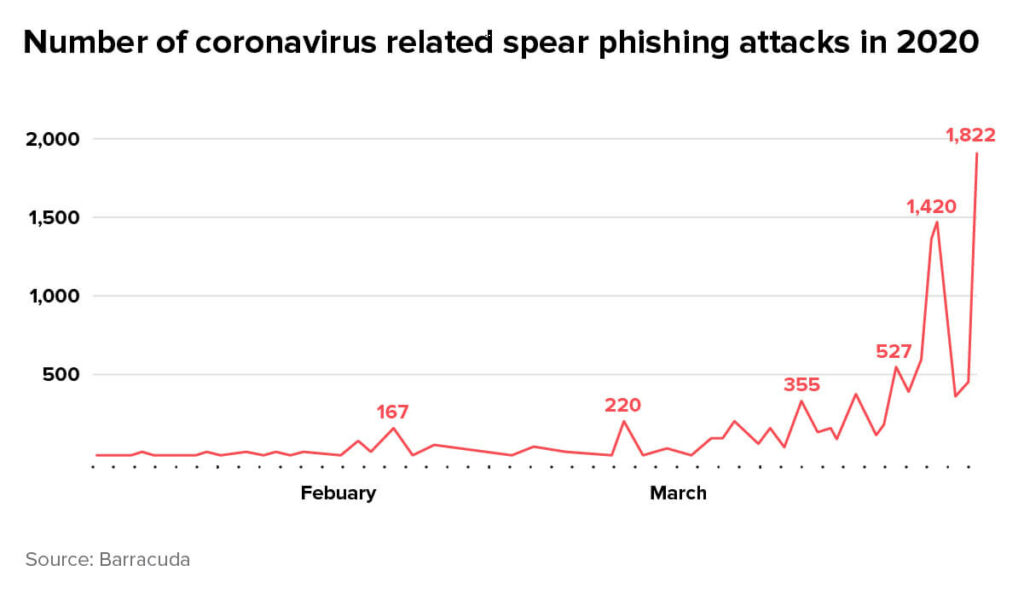
Fraudsters are keen to capitalize on the environment of fear and panic that’s taken hold of the world, using the virus as a ploy to lure unsuspecting victims into sharing their personal and financial information. Scams in general – and phishing attacks in particular – are reaching astronomical proportions. According to one study, the number of spear phishing attacks – those targeting specific people or companies – grew 667% in March compared to the previous month.
In this blog post, we’ll identify five types of attacks that are hitting people and businesses during the pandemic, explain why this is happening and offer our insight on mitigating the fallout.
Types of Cyberattacks on the rise during Coronavirus
Phishing attacks
- Government Impersonators – Fraudsters disguising themselves as government agencies, such as SSA, IRS, and WHO, send emails and text messages to victims to collect personally identifiable information.
- Website & App Spoofing – These attacks involve the creation of a fake website or app designed to look like the login page for online stores, apps, and services such as Netflix. Fraudsters send emails linking to cloned websites and apps, luring people to enter their login credentials.
- Business Spoofing – Using an emulated email address, fraudsters disguise themselves as a high-ranking manager within an organization and send emails to employees, requesting credentials, or ordering payouts. Fraudsters are capitalizing on the environment of confusion and limited communication when employees work from home.
Malware – Short for malicious software, malware usually arrives in the form of a disguised email attachment or as a fake phone app. Once downloaded, it steals information from victims and sends it to the criminals, and can spread to other computers on the same network. Even frontline medical organizations aren’t safe: the John Hopkins Coronavirus dashboard has been emulated by fraudsters to steal PII from innocent victims, while medical institutions and research facilities have been hit by malware in Canada and Japan.
Ransomware – Also disguised as a phone app or email attachment, ransomware steals the victim’s information and locks them out of their computer or smartphone until they transfer money to the criminals in the form of cryptocurrency.
Why is this happening?
First and foremost, cybercriminals are professional when it comes to exploiting fear and panic. In this state of global chaos, emotional vulnerability is high. People are scared for their health, their finances and their loved ones, leaving them exposed to fictitious claims of relief.
Secondly, with lockdowns in place across the globe, internet usage has soared. Computers and smartphones have become the go-to method for accessing news and information, socializing remotely with loved ones, consuming entertainment and purchasing goods. The more time people spend online, especially on social media, the more they expose themselves to potential cyber threats. Particularly vulnerable are older shoppers, who don’t normally buy online and are less familiar with scams and how to spot them.
Also particularly vulnerable are the massive amounts of people working from home. Businesses are opening their networks for external access to allow for remote work, making security and control harder to maintain. Data stored by businesses is a lucrative target for fraudsters, who are quick and eager to take advantage of the situation.
What are the expected consequences?
Phishing attacks are often the starting point for account takeover (ATO) attacks. Once a victim has entered their email and password into a cloned site, fraudsters take those credentials and use them to hack into the victim’s account. These attacks are lucrative for fraudsters, who bank on the victim’s existing relationship with the merchant, including a history of good orders, to help them bypass stringent fraud prevention measures. Particularly at risk are those accounts with a stored payment method, which can be used to commit fraud without requiring additional information.
Larger data breaches, including those committed using malware or ransomware, can lead to CNP fraud when payment details and personal information are exposed and stolen. Bots are often used to run through large batches of credit cards and find those that work. The fraudsters make small, insignificant purchases, allowing them to verify the information they have and ensure the credit card is still active, without setting off alarms. The information is then sold on the dark web and used to commit more significant fraud attacks.
Unfortunately, the full implications of these large-scale attacks may not be apparent for months to come, as fraudsters wait patiently for businesses and cardholders to lower their vigilance before carrying out an attack.
Beyond the realm of fraud, the heightened awareness around Coronavirus scams might lead some customers to mistrust legitimate authentication methods. Two-factor authentication, for example, often in the form of a text message requesting additional information, might be misinterpreted as a scam and treated with suspicion, which could increase the risk of cart abandonment.
What can be done to protect your business and customers?
As Coronavirus-related cybercrime becomes increasingly common, law enforcement agencies around the world are working to fight them. Europol has closed 2,500 websites in 90 countries; the FBI issued a warning and continues to monitor threat levels; even the World Health Organization has opened a reporting line for scams impersonating the organization.
With the eCommerce market so volatile during this outbreak, agility and flexibility have never been more important. Merchants need to limit the impact of fraud by leveraging technology to protect themselves and their customers. Specifically, your fraud prevention solution should:
- Detect behavioral changes associated with ATO attacks. Fraudsters act differently from legitimate customers logging into their accounts. Familiarize yourself with the behavioral indicators of account takeover attacks, such as cross-referencing the login device or IP against previous orders from the same account to pick up on any irregularities. Merchants should also enter into a data-sharing program with other businesses, which would allow them to extend their network and cross-reference logins and transactions with previous orders from other stores.
- Be adaptive. Fraud prevention solutions that are based on machine learning are better equipped to adapt to changing shopper behavior – and emerging fraud patterns. Since the start of the pandemic, consumer behavior online has changed significantly, including an influx of new customers who are forced to shop online because they can’t go to the store. Legacy fraud solutions that depend on consistent shopping patterns to distinguish friend from foe run the risk of falsely declining good customers, and failing to recognize new fraud patterns that have cropped up during the crisis. Make sure your machine learning models are constantly evolving to capture trends in the eCommerce landscape.
- Monitor for specific patterns that may indicate card testing. Multiple purchases of very low-ticket items can be an indicator of this kind of activity. Particularly vulnerable are the donation sites of non-profit organizations. These sites are targeted because giving an online donation does not require a shipping address, and because fraudsters know non-profits are unlikely to have sophisticated fraud detection safeguards in place.