3D Secure 2.0: What to Know
3D Secure or 3-D Secure? 3D Secure 1.0. or 3D Secure 2.0? 3DS or EMV 3DS?
The alphabet soup of payment authentication protocols has been more visible in the press and general eCommerce and payments buzz lately. Why? Because the latest update of a decades-old card-not-present payment authentication protocol launched earlier this year. Plus, PSD2 is going into effect on September 14th for merchants, and one aspect of this European regulation requires merchants and card networks to authenticate shopper identity in order to transact online.
In this post, I will break down what these acronyms are, which merchants they are relevant for, and what merchants must consider before deciding to add these protocols to their checkout flows.
What is 3D Secure?
3D Secure, also referred to as 3-D Secure, 3DS, or 3-D Secure authentication, stands for three-domain secure. It is a security protocol that adds a layer of authentication in the online card-not-present checkout process to verify cardholders’ identity prior to authorization. The purpose of 3DS is to protect a shopper’s credit card against unauthorized use when shopping online. To do so, it involves three parties — or three domains: the acquiring bank (or the merchant’s bank), the issuing bank (or the cardholder’s bank), and the infrastructure supporting this protocol, such as the internet, merchant plug-in, and other software providers.
The first iteration of 3DS — also known as 3DS1 or 3DS 1.0 — was created in 1999, the early days of eCommerce when the personal computer was the only online shopping channel available. Card networks implemented 3DS1 in 2001 under branded names such as Verified by Visa or Mastercard Identity Check.
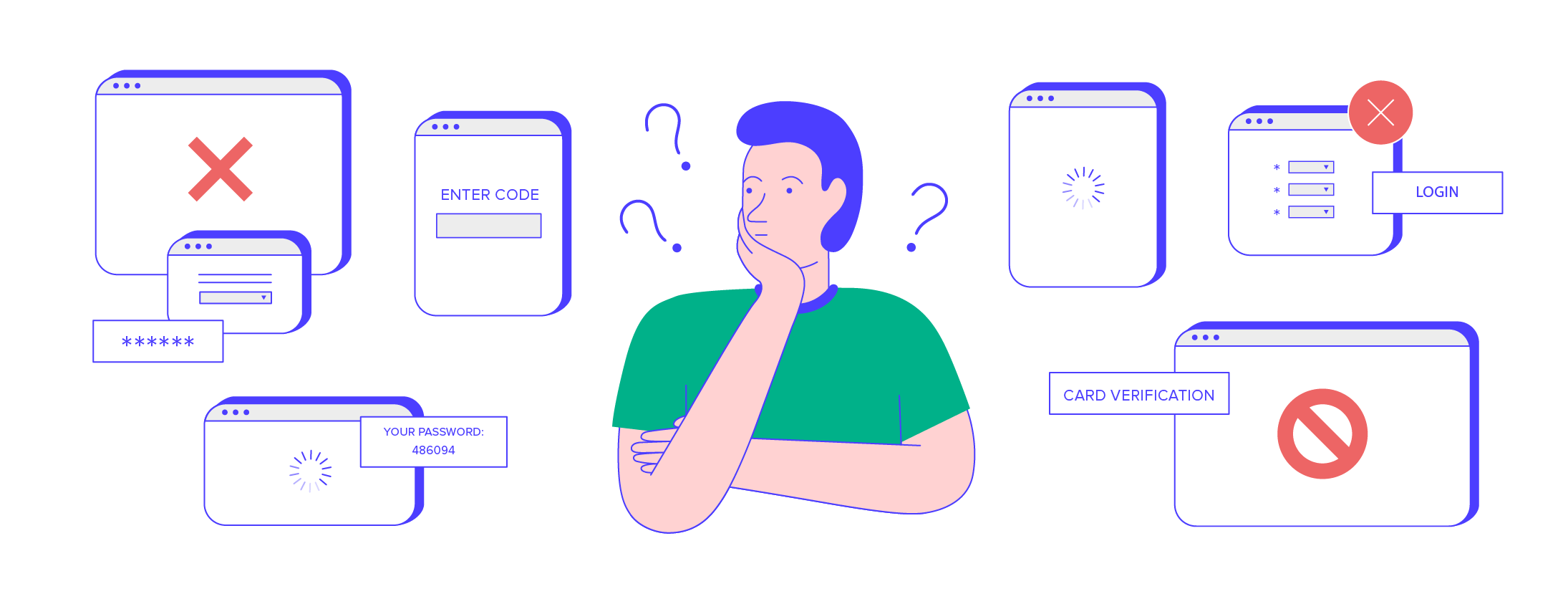
It works like this: after consumers enter their card details to confirm payment to an online merchant, issuing banks determine the fraud risk of transactions based on up to 15 basic data points such as the currency used in the transaction and the web browser user-agent. If determined risky, a pop-up window or inline frame would appear, requiring the consumer to enter a password to verify their identity with the bank that issued their card.
Consumers need to enroll in 3DS1 to have a static password or code to authenticate themselves. Those who aren’t enrolled are directed away from the merchant’s checkout page to the issuer bank’s website so they can register and set up credentials. Should the consumer refuse to enroll beyond a designated number of opt-outs, s/he could be banned from making purchases online at retailers that use 3DS pending enrollment.
The biggest upside for merchants in using 3DS was the liability shift with simultaneous promise of reduced fraud. By having cardholders authenticate themselves to the bank that issued their credit or debit card, fraud responsibility shifted away from the merchant and toward the card issuer, reducing chargebacks to the merchant.
Unfortunately, the promise was not quite fulfilled. Issuers would take the ‘better safe than sorry’ approach, by opting to err on the side of caution and declining a transaction to avoid potential fraud. This contributed to as much as $118 billion lost in 2014 to false declines across all online transactions. Part of the reason why issuers struggled with false declines is that they only had visibility into 15 data points instead of the broader range of information that merchants gather on a shopper throughout the customer journey. Merchants also had no access to information or analytics on shoppers post-checkout, as the data was captured directly from the cardholder’s browser without passing through the merchant’s system.
Another limitation for merchants was that once they decided to use 3DS1, they had to use it for all transactions where 3DS was supported. This lack of flexibility led to some merchants dropping 3DS all together.
But there was an even bigger problem: this checkout flow was so clumsy and outdated that it led to merchants losing the sale and issuers losing the transaction. 3DS1 was designed only for web-browser authentication, and couldn’t support shopping on mobile devices. Plus, the use of static passwords to enroll customers into 3DS1 created a clumsy user experience that led to shopping cart abandonment as well as increased operational costs for issuers, due to customer calls requesting password resets
By 2017, only 18% of US-based transactions leveraged 3DS. There was so much friction that 3DS cart abandonment rates were higher than 50% in countries such as Brazil. What made matters worse is that all that friction didn’t even make 3DS 1.0 effective at reducing fraud. The Federal Reserve Bank of Minneapolis found in a survey two years ago that less than one third of banks with $1 billion or more in assets rely on 3DS or its equivalent.
3-D Secure 2.0 arrives… nearly two decades later
In order to address the many shortcomings of 3DS1 and the changing regulatory landscape for eCommerce and card-not-present transactions, EMVCo, an organization made up of six major card networks, released a new version of 3DS: 3D Secure 2, also referred to as EMV 3-D Secure, 3-D Secure 2.0, 3D Secure 2.0 or 3DS2. Issuer banks have aimed to complete 3DS2 integrations by spring 2019.
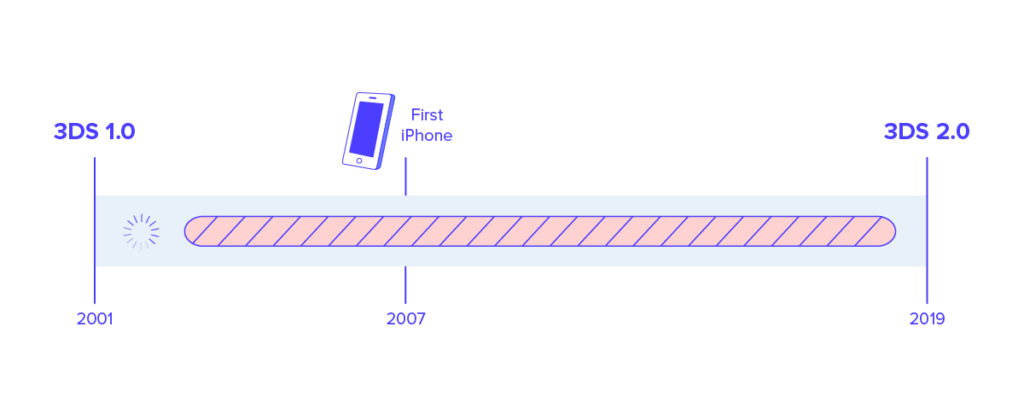
3DS2 is the first update since 2001, six years before the iPhone was first introduced and nearly 20 years since the protocol was first created. Pause here to contrast that with how often you have to update your smartphone apps and operating systems these days.
EMVCo claims the biggest changes from 3DS1 to 3DS2 is a better user experience while reducing fraud. Instead of a static password, users can authenticate with a one-time passcode sent to a mobile number associated with the account or biometrics such as thumbprint, face or voice recognition. The technological update creates a data connection between merchants, payment networks and financial institutions to analyze up to 150 data elements, and share more intelligence about transactions. 3DS2 can now support mobile apps as well as browser-based environments.
To adopt or not to adopt 3DS2?
3DS2 is most relevant for merchants who need to be compliant with government regulations, namely the Payment Services Directive. The directive, more commonly known as PSD2, will go into effect on September 14, 2019. It mandates Strong Customer Authentication (SCA), or two-factor authentication for electronic payments. PSD2 applies only to EU-to-EU payments, which means 3DS2 is relevant only for merchants with exposure to the European market. You can read more in-depth about protecting your revenue under PSD2 here.
For merchants who have no presence in Europe or any other markets where two-factor authentication such as 3DS is required, the protocol’s value is more questionable. That is why less than 2% of North American eCommerce transactions and fewer than 5% of Australian transactions use 3DS today, according to Aite Group.
PSD2 or not, card networks are marketing 3DS2 as a friction-less solution to card-not-present online fraud. They claim 3DS2 will reduce false declines and increase approval rates, but there are 5 things merchants should take into consideration when shopping for a standalone, end-to-end fraud management system:

1. Adaptability to rapidly-changing marketplace and industry
As mentioned earlier, card networks have not evolved their fraud review technology for nearly 20 years. One of the biggest selling points for 3DS2 is that negative feedback on 3DS1 have all been incorporated into technical adjustments that increased the number of data points issuers review 10 fold. Just because issuers are now able to review higher quantity of data, that doesn’t necessarily mean that they know how to make sense of it, how to manage it, and what to do with it.
A lot is at stake for merchants to trust their revenue with card networks that haven’t innovated for decades, and issuer banks that are still in the process of integrating 3DS2. How can merchants know that 3DS2 is ready for prime time without any glitches to work out?
2. Conversion rates
Visa, Mastercard and other card networks pledge to improve approval rates and reduce cart abandonment and shopper drop-off rates, but have no tangible performance data to prove 3DS2 will deliver.
The majority of issuers need to migrate to 3DS2 before we can get hard data, and that can take a while. What we already know is that, in most cases, 3DS2 will still add another step to the payment journey, potentially ostracizing legitimate customers. Merchants know better than anyone just how lethal an extra step can be to the checkout process.
3. True liability shift?
One major attraction for merchants to 3DS has been the liability shift for fraudulent chargebacks to card issuers. However, the shift under 3DS doesn’t cover all transactions.
For Visa and Mastercard, 3DS can result in 5 scenarios: authentication successful, authentication attempted, authentication failed, authentication unavailable, and error. Liability shift happens only when authentication was successful, followed by a chargeback. If authentication fails, an error occurs, or if authentication is unavailable, the chargeback liability stays with the merchant.
There’s also a distinction in liability shift rules, depending on which card provider a merchant works with. When a specific card is not enrolled in 3DS, Visa takes responsibility for any fraudulent chargebacks. With Mastercard, the responsibility stays with the merchant. These “rules” can get tricky, and we strongly advise merchants to check with issuing banks on the distinctions.
4. Research providers
Merchants need to do their due diligence on 3DS vendors (gateways and payment processors). The merchant is sharing more data points with issuer banks than they used to with 3DS1. Merchant should check whether they can access the valuable post-checkout transaction data that gets processed through 3DS2. The number of times a shopper was presented with the 3DS verification page and the percentage of orders that were protected can give valuable industry insights into customer behavior. That information can also provide fraud analysts with important statistics on fraudulent activities.
So make sure to ask how securely vendors will handle valuable data you will share, and how much more insight you will get back. Also ask whether vendors will support both 3DS1 and 3DS2? Will vendors ensure easy integration with your eCommerce platform?
5. Lack of experience
We cannot belabor this point enough: can you trust the accuracy rate of card issuers who simply haven’t had that much practice processing more than 15 data points per transaction to determine legitimacy? And how much transparency will merchants have into the issuer’s decision process?
Knowledge is power. Merchants should do their research on whether 3DS is suitable and sufficient for their needs, and fact check all that 3DS2 claims to offer. Trust and safety are critical for merchants to ensure that their brand and hard-earned revenue is safeguarded. Reach out to learn more about leading merchants who trust Riskified to approve more orders, assume chargeback liability and manage risk.


